As reported by WIRED immediately, a bunch of six laptop scientists this yr found a safety vulnerability with the Apple Imaginative and prescient Professional that allowed them to reconstruct what individuals have been typing, together with passwords, PINs, and messages.

When a Imaginative and prescient Professional person was utilizing a digital Persona avatar, equivalent to throughout a FaceTime name, the researchers have been capable of analyze the Persona’s eye motion or “gaze” to find out what the person was typing on the headset’s digital keyboard. The researchers created an internet site with technical particulars in regards to the so-called “GAZEploit” vulnerability.
Briefly, the researchers mentioned that an individual’s gaze sometimes fixates on a key they’re more likely to press subsequent, and this could reveal some widespread patterns. Because of this, the researchers mentioned they have been capable of establish the right letters individuals typed in messages 92% of the time inside 5 guesses, and 77% of the time for passwords.
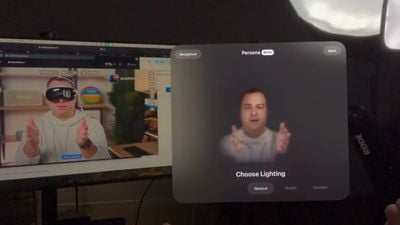

The researchers disclosed the vulnerability to Apple in April, in line with the report, and the corporate addressed the problem in visionOS 1.3 in July. The replace suspends Personas when the Imaginative and prescient Professional’s digital keyboard is lively.
Apple added the next entry to its visionOS 1.3 safety notes on September 5:
Presence
Accessible for: Apple Imaginative and prescient Professional
Affect: Inputs to the digital keyboard could also be inferred from Persona
Description: The problem was addressed by suspending Persona when the digital keyboard is lively.
CVE-2024-40865: Hanqiu Wang of College of Florida, Zihao Zhan of Texas Tech College, Haoqi Shan of Certik, Siqi Dai of College of Florida, Max Panoff of College of Florida, and Shuo Wang of College of Florida
The proof-of-concept assault was not exploited within the wild, in line with the report. Nonetheless, Imaginative and prescient Professional customers ought to instantly replace the headset to visionOS 1.3 or later to make sure they’re protected, now that the findings have been shared publicly.


