Malware is unhealthy software program you do not wish to encounter, as it might hurt your Mac or trigger information loss. Here is tips on how to shield towards it.
With safety being an ever-increasing concern within the linked age, malicious assaults by unhealthy actors proceed to be an issue for a lot of organizations and customers.
Malignant software program (malware) will be planted in your units, which may result in credential or information loss, corruption of working techniques, or ransomware.
As billions of digital units proliferate worldwide and extra commerce strikes on-line, malware has change into an ever-increasing menace.
Software program safety fashions
Within the early days of software program – earlier than the web turned mainstream, most techniques had been open and software program may very well be put in from anyplace. Often it was from CD-ROM or floppy disk.
With on-line software program shops now the usual, it is a little much less of a problem. It is because app storefronts test most software program earlier than it’s launched to make sure safety.
Nonetheless, unhealthy software program can and does typically slip by way of.
Apple tried to resolve this downside with the introduction of curated shops, such because the iOS App Retailer. However even there, some unhealthy software program has sometimes been launched.
Curated shops are safer and dependable, however they’re nonetheless not foolproof.
The Mac is barely completely different, as a result of in its early days, it too might settle for software program from any supply. Traditional apps equivalent to Virex and Norton Utilities helped “clear” Macs of malware.
The Mac App Retailer right this moment options curation, app receipt validation, and app notarization. However the Mac nonetheless permits software program set up from anyplace, if sure settings are turned off.
Code Signing, Developer ID, and Gatekeeper
Years in the past, Apple launched an extra safety measure for macOS software program: Gatekeeper. Together with Developer ID, Gatekeeper by default ensures that downloaded Mac software program is safe.
With Gatekeeper, macOS builders register with and are issued a Developer ID by Apple, which is then used to digitally signal Mac software program they create.
If Gatekeeper is turned on in macOS, it ensures apps are signed by the builders who make them. It additionally warns on a Mac app’s first-run for apps that are not from identified, registered builders.
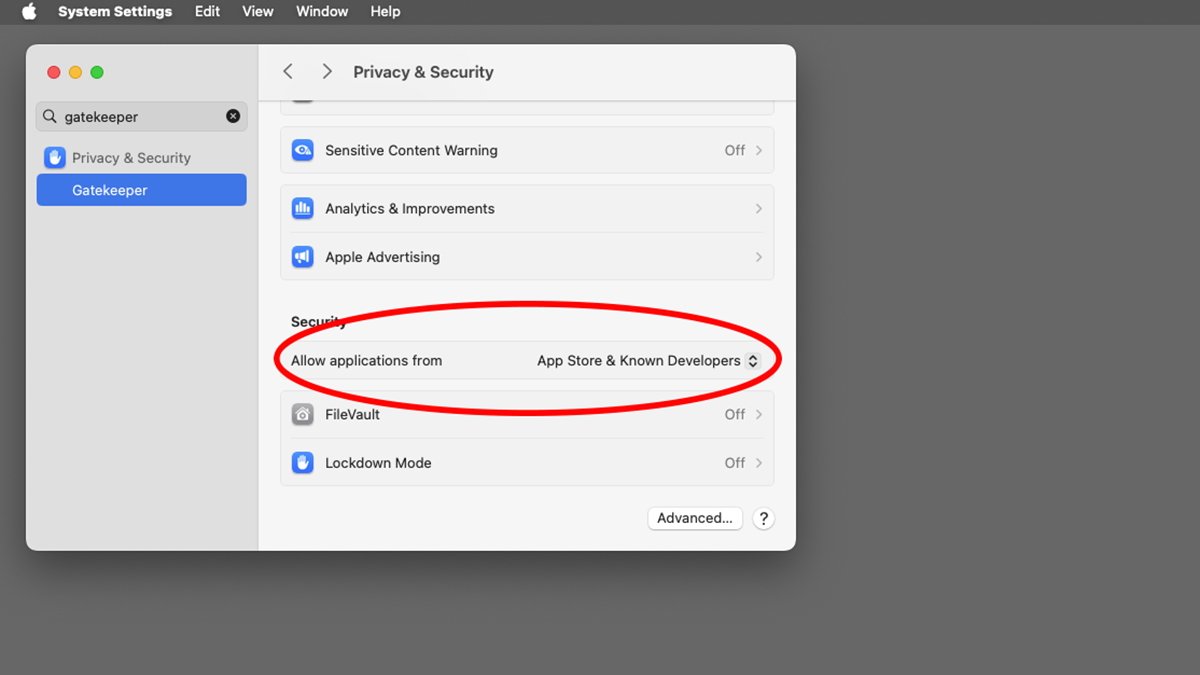
Mac customers can select in System Settings->Privateness & Safety->Enable Functions from which apps they wish to permit set up for: both App Retailer-only apps or App Retailer & Identified Builders.
Code Signing Companies and app Notarization make sure the software program is legitimate and never hacked or malicious when customers obtain it.
System Integrity Safety (SIP)
SIP restricts which apps will be allowed to run and what code will be run on Macs. By default, solely App Retailer apps or software program from registered Apple builders can run.
It additionally restricts system information from being tampered with or modified with out authorization.
It’s attainable to show off SIP within the Terminal, nevertheless it’s not really useful. Doing so defeats the safety of macOS and should permit malicious code to run on Macs.
The csrutil command-line software can be utilized to examine and alter SIP parameters.
To get the present standing of SIP in your Mac in Terminal kind:
csrutil standing and press Return.
Most UNIX software program makes use of the idea of privileges and privileged customers. The root person, for instance, has limitless safety privileges and may make modifications to software program at will.
For safety causes, the basis person is disabled by default in macOS. Different customers might produce other various ranges of privileges, which permit sure actions together with software program set up or elimination.
admin customers have elevated privileges, and an admin password is required for a lot of operations in macOS.
Through the use of short-term privilege escalation, macOS customers will be granted extra rights for a brief time period.
Properly-designed software program needs to be factored in order that security-critical code runs in a separate course of known as a helper software. Helper instruments be sure that solely small elements of code will be run with elevated privileges – thus proscribing which elements of software program can carry out crucial duties that may endanger the system’s safety.
An app with good factoring will put all at-risk code right into a helper software, then when permissions are wanted run the helper software after the person has been approved. This will increase safety and in addition means compromised apps cannot run all code at elevated privileges – which is a safety danger.
The thought is to run the helper software and elevate privileges for the least period of time, carry out privileged operations, after which drop privileges again to their earlier degree when the helper software exits.
UNIX area sockets and pipelines may also be used to securely cross data between processes.
Safety daemons and frameworks
macOS is likely one of the most safe working techniques on the planet, nevertheless it’s not foolproof.
Safety in macOS is managed with a mixture of background processes (daemons), and Apple code frameworks loaded into apps when they’re run. These embody:
- launchd
- secured (the safety server)
- XPC Companies
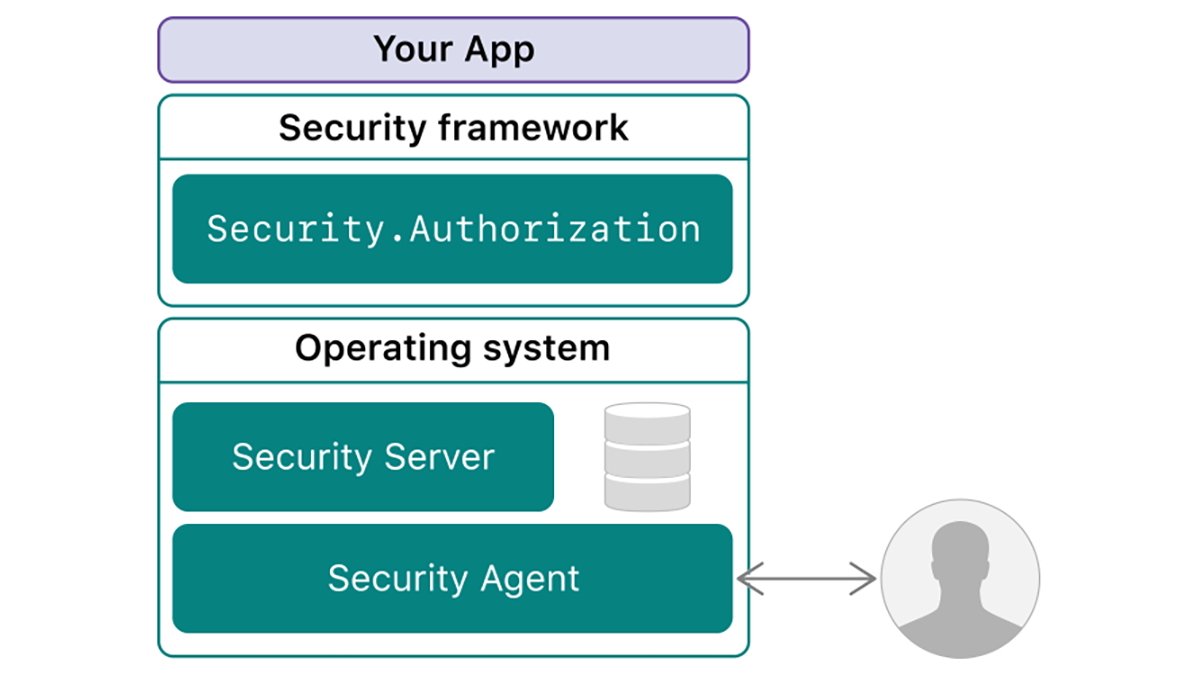
- Authorization Companies.framework
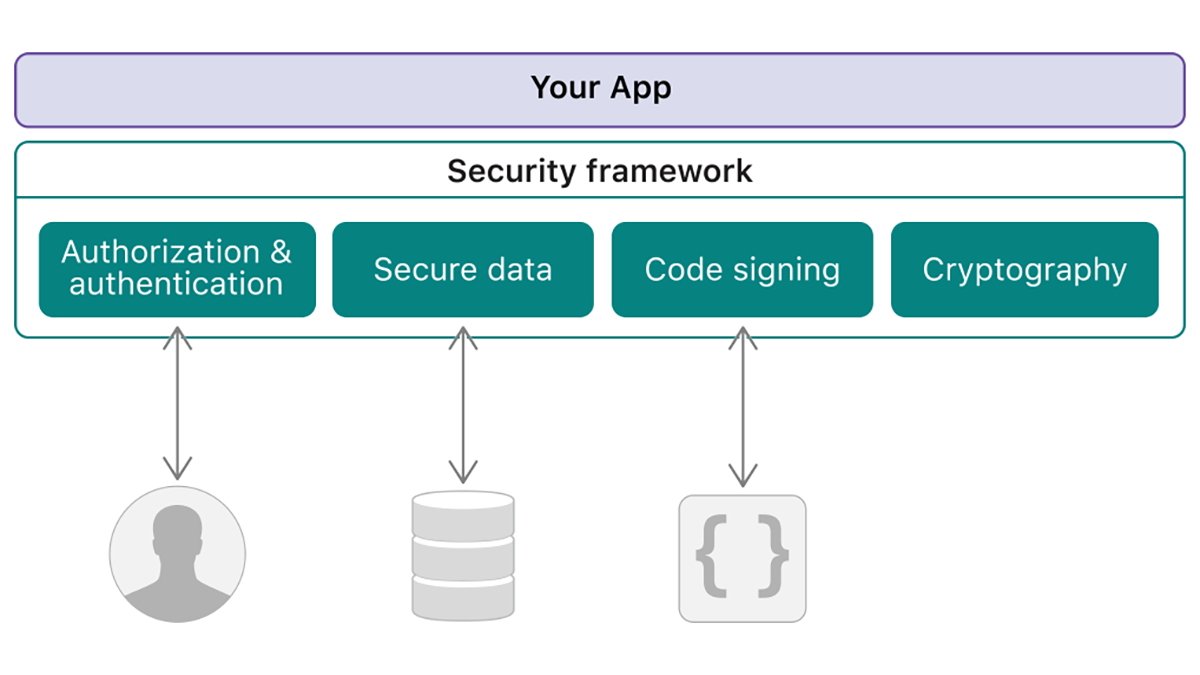
- Safety.framework
- System Configuration.framework
- Service Administration.framework
- Endpoint Safety.framework
- Cryptographic Companies
- Code Signing Companies
- Keychain Companies
- Hardened Runtime
Dynamic linking ensures frameworks are solely loaded into reminiscence when their APIs or interfaces are literally used.
The above software program elements present the next companies:
launchd (the Launch Daemon) is a system-wide daemon that runs within the background and manages the launching and termination of apps and different processes in macOS.
secured (the Safety Daemon) manages safe entry, elevating privileges, operating instruments and sure person IDs, and different safety companies.
XPC Companies manages safe interprocess communication between software program elements in addition to working with launchd to run helper instruments securely.
Authorization Companies.framework manages prompting customers for an admin password, caching privilege escalation, and sustaining timers which decrease privileges after a given timeout. When your Mac prompts you for an admin password to put in software program or change a setting, it sends a message to secured to show the admin password dialog field so the person can enter a reputation and password.
Safety.framework manages person identification (authentication) and grants entry to sources, secures information on disk and throughout community connections, and verifies the validity of code earlier than it runs.
System Configuration.framework manages system settings and ensures restricted settings can solely be modified if required authorization has been supplied.
Service Administration.framework permits apps to handle launch brokers, launch daemons, and login gadgets.
Cryptographic Companies gives normal cryptography APIs, manages keys, certificates, and passwords, and generates random numbers and hashes.
Code Signing Companies gives companies to signal and confirm constructed software program to make sure it is legitimate and hasn’t been compromised.
Keychain Companies manages system keys, certificates, and identities.
Hardened Runtime (together with SIP) protects macOS from code injection, reminiscence tampering, and dynamic library hijacking. Apple’s Xcode IDE consists of Hardened Runtime settings together with permitting or disallowing Simply-In-Time (JIT) code, use of unsigned reminiscence, and dynamic linker (DYLD) setting variables.
Altering setting variables earlier than operating malware is a technique malicious code will be injected into operating apps.
All of those elements work collectively to make sure macOS software program will be as safe as attainable.
The safety idea of Zero Belief implies that all privileged software program entry is restricted until a privileged person explicitly authorizes some safe motion. Zero Belief implies by default that malware cannot run with out particular authorization.
You’ll be able to see which daemons are at present operating in your Mac within the Exercise Monitor utility, or through the use of the high command in Terminal. To make use of high kind:
This shows all operating processes – together with daemons, course of IDs (PIDs), runtimes, CPU use, ports, and extra.
Malware on Macs
Malware will be outlined as malicious software program that may breach or infect a pc, community, or system to disable, corrupt, or injury a tool, or to steal and transmit unauthorized information throughout a community.
The Pc Fraud and Abuse Act makes it a federal crime within the US to tamper with, disable, or achieve entry to a pc or community with out particular authorization. It additionally makes transmitting or intercepting stolen data throughout a community against the law.
Sorts of malware embody (however aren’t restricted to) viruses, Trojan horses, malicious apps or frameworks, drivers, and even firmware. Community assaults are additionally attainable by injecting malware into community code, or listening in on community communications.
Ransomware is malware that steals firm commerce secrets and techniques or buyer information, then permits unhealthy actors to demand a fee from a corporation to not use or launch the stolen information.
Viruses are small items of code that may be put in and run remotely on a person’s native laptop and wreak havoc silently.
Viruses can corrupt or modify utility code, drivers, information, databases, or system software program to carry out some malicious exercise. This may embody erasing/damaging information, or modifying software program to carry out some malicious act.
Viruses will be silent, undetectable, and tiny – and sometimes go unnoticed till it is too late. As a result of viruses will be put in nearly anyplace, they’re exhausting to cease and even more durable to eliminate as soon as they infect a pc or system.
Prior to now, viruses have even been identified to contaminate the firmware of units equivalent to storage drives or community routers, rendering them completely broken and unusable.
A Malicious program is usually thought-about to be an app which, when run harms saved information or different put in software program and causes it to carry out some malicious exercise. One widespread assault vector of Trojan horses is to silently substitute software program frameworks or system elements with a malicious impostor model, which linked apps then unwittingly run.
Trojan horses make regular apps unaware that when hacked framework APIs are known as the impostor will trigger injury. Trojan horses typically come within the type of standalone apps or installers, or frameworks and linked libraries.
Gadget drivers, likewise will be put in to run malicious code when a particular system is used. Community malware drivers are particularly infamous since they’ll transmit information at will over a community – which may’t be retrieved or “unseen” as soon as despatched.
Malicious firmware infects or replaces present firmware inside exterior units, inflicting them to wreak havoc upon regular operation, or when particular normal instructions are despatched to a tool. Malicious storage system firmware might be the most typical, since it might simply be put in through flash instructions within the system – after which trigger normal disk I/O instructions to set off information loss or corruption.
Community assaults come within the type of malicious code injected into internet pages or database instructions, often by including extra code on the finish of normal instructions and information.
Buffer overflow malware for instance appends a small quantity of malicious code to the top of a URL, internet web page, script, or community packet – which when obtained and run on the shopper laptop causes injury.
Buffer overflow assaults are one of the vital widespread web-based assaults. They’re exhausting to detect as a result of most community code and internet pages run mechanically and outdoors of most software program safety fashions.
Most internet browsers now embody settings for proscribing what sorts of software program will be downloaded and run mechanically of their home windows.
Java applets are significantly well-known for enabling malware downloads.
Different sorts of community assaults embody impostors, man-in-the-middle, credential theft, phishing, e mail spoofing, and Distributed Denial of Service (DDoS) during which distant computer systems flood servers with a lot information they cease working.
Social engineering assaults are misleading techniques during which unhealthy actors persuade victims they’re respectable to be able to achieve entry to their protected data, or trigger them to take some motion which could hurt them. Social engineers may additionally attempt to manipulate victims into unwittingly performing crimes, in order that within the occasion they’re caught they’ll blame another person.
Social engineering specifically is used within the huge and largely unknown area of industrial espionage (spying).
What you are able to do
Because of the well-thought-out macOS safety mannequin and UNIX privileges, the Mac is a really safe system. Nonetheless, breaches can and do occur.
Because of the disabled root person and restricted privileges which most Mac software program runs beneath, it is exhausting for an attacker to trick macOS into operating malicious code with elevated privileges. Signed and safe helper instruments make these makes an attempt much more tough – and guarantee most malicious software program cannot dangle round lengthy sufficient to do severe injury.
Beneath the watchful eyes of secured and launchd, tricking a bit of Mac software program into operating at full permissions with out an admin password is tough. It is also exhausting to defeat secured itself since it might solely run as a sure OS-controlled person with elevated privileges – and with out it different safe software program cannot be approved to run.
Apple removes most malicious software program from its app retailer rapidly So long as SIP is enabled, software program from non-authorized registered Apple builders cannot be run and not using a person warning.
You can too run numerous “cleaner” apps to scan your Mac and storage units for malware. However be cautious – even cleaner apps have been disguised as malware prior to now!
Periodic virus scans and eradicating suspect apps out of your Mac might assist scale back danger. One other good coverage is to easily preserve the variety of apps you put in to a minimal, thus narrowing the assault floor.
You may wish to set up little-used software program on a single exterior drive – after which solely plug the drive in when you should entry that software program.
Protecting system extensions, scripts, third-party fonts, drivers, and kernel extensions to a minimal can be a good suggestion – this can even scale back background job overhead.
You may think about setting your internet browser’s safety to its highest degree, and turning on blocking of suspected malicious websites by default. This may also help scale back the likelihood {that a} community assault from a malicious website can hurt your Mac.
Some browsers have settings that block all downloads of internet applets to guard towards harmful Malicious program downloads.
Additionally, make sure all WiFi passwords and entry factors in your networks are safe – and do not permit nameless logins. Some Mac community settings will let you require an admin password to vary the settings.
You should definitely prohibit admin customers in your Mac – solely giving admin permission to customers who completely want it, and just for the size of time required. By default, most customers in your Mac should not have admin entry.
You may also wish to preserve Visitor customers disabled. Enabling Visitor customers permits any distant person to connect with your Mac and not using a password.
Additionally preserve Distant Administration, Distant Login, and Distant Utility Scripting turned off in System Settings->Sharing until you completely want them.
Gatekeeper and runtime safety
In the event you obtain and run a non-App Retailer piece of Mac software program that is not from a certified Developer ID, macOS will warn you and ask should you’re positive you wish to run it. That is achieved by part of macOS known as Gatekeeper.
In the event you’re sure you wish to run the software program, you’ll be able to click on Enable within the Finder’s alert field, which is able to permit the software program to run. This straightforward safety test offers you an additional probability to confirm the software program earlier than it blindly runs on the primary double-click.
Limiting apps to solely App Retailer apps in System Settings means you’ll be able to solely set up and run App Retailer apps in your Mac. This may forestall all attainable third-party apps downloaded exterior the App Retailer from operating – however you’ll be extra restricted in your software program choice in consequence.
For background and historic information on how daemons and brokers work on the Mac, see TN2083
Apple has taken nice pains to design and construct macOS to be safe – and typically, you will not want to fret about safety in your Mac. However preserve the entire above in thoughts as you employ your Mac to make sure the prospect of being hit by malware is as small as attainable.