Apple units use many frequent web safety requirements. Here is what every of them does, and find out how to use them in your Apple {hardware}.
Within the networked world we reside in, web connectivity is ubiquitous.
Holding community communications safe is likely one of the most essential facets of web know-how. Over the a long time, a number of totally different requirements have developed to maintain networks and units safe.
On this article we’ll take a look at a number of of those requirements, and the way they relate to Apple units.
IPsec, IKEv2, L2TP
Three key applied sciences are used for safe connections and VPNs: IPsec, IKEv2, and L2TP.
IPSec is a safety customary which was born of early DARPA ARPANET analysis. It was later formalized by MIT, Motorola, and NIST.
IPSec is generally utilized by VPNs, offering safe authentication, key change, encryption, and information integrity features. In the event you’ve ever put in VPN software program on one in every of your Apple units, you’ve got used IPSec.
It’s thought-about a “Layer 3” protocol which sits atop Layer 2 protocols, which we’ll see in a second.
IKEv2 is the Web Key Trade protocol. There are three variations this protocol: IKE, IKEv1, and IKEv2.
It’s utilized in IPSec and by DNS to create and change safe key pairs throughout connections. Shared keys are a part of Public Key Infrastructure (PKI) which eliminates the necessity for passwords.
IKE relies on two earlier protocols: The Oakley protocol and ISAKMP. These protocols got here out of efforts within the late 1990’s to safe web connections when it grew to become clear early web communications had been insecure in lots of situations.
The Oakley protocol makes use of the now-famous Diffie-Helman Key Trade algorithm to securely change keys for encryption.
ISAKMP is a key change framework that gives a safety affiliation and keys for use by key change protocols reminiscent of IKE. Cisco adopted each the Oakley and ISAKMP protocols to be used in most of its VPN and router merchandise.
There are different key change protocols, reminiscent of Kerberized Web Negotiation of Keys (KINK) and SKEME.
L2TP, or Layer 2 Tunneling Protocol is a tunneling protocol used for management messages throughout community communication. L2TP does not safe or encrypt information or content material itself, it solely encrypts the management indicators utilized in connections.
This protocol was formalized in 1999 within the RFC 2661 specification which was shaped because of Cisco’s L2F protocol and Microsoft’s PPTP protocol. It additionally makes use of the Person Datagram Protocol (UDP) throughout packet transmission.
UDP has the principle benefit of being an acknowledgment-free broadcast protocol, for which listeners wait on a sure port for data with out having to answer to the sender.
L2TP took place as a necessity for safety for PPP (Level-To-Level Protocol) when dial-up modems had been nonetheless in widespread use. Information packets will be transmitted over a Layer 2 tunnel through the use of one of many different extra encrypted protocols.
Safe tunneling ensures any information touring within the tunnel is encrypted and managed between solely two factors. This makes replay and man-in-the-middle assaults tough for attackers to execute.
L2TP is used principally in company VPNs for safe entry.
Many VPN apps can be found for Apple units, by way of the App Retailer. Most Apple working techniques additionally present built-in options for simply including VPN profiles to units.
IPsec, IKEv2, and L2TP function principally behind the scenes, and until there’s some particular setting you must change, you will normally by no means have to trouble your self with them.
TLS, SSL, and X.509 certs
When the online first went mainstream within the late Nineties, it rapidly grew to become obvious that every one internet communication wanted to be encrypted. All in order that information could not be intercepted and listened to between browsers and servers.
Because of this Safe Sockets Layer (SSL) was developed. Now referred to as Transport Layer Safety, this protocol encrypts most site visitors between internet browsers and servers.
The “s” in “https” stands for “safe” – and signifies that you’re looking an internet site by way of a safe connection.
SSL/TLS can be utilized in some safe e mail communications. TLS was additionally proposed in 1999 and has undergone three revisions, the present model of which is TLS 1.3.
SSL was initially developed in 1994 for the primary variations of Netscape’s Navigator browser, which in the present day has morphed into Mozilla Firefox. There may be additionally a Datagram Transport Layer Safety (DTLS) protocol.
TLS makes use of X.509 certificates to change data utilizing encryption and encrypted handshakes. As soon as the handshake completes, the server normally supplies the consumer app with a certificates so sever will be trusted.
X.509 certificates enable a consumer app to confirm the authenticity of the server, in order that impersonation assaults cannot work. The X.509 customary is outlined in RFC 5280 by the Worldwide Telecommunications Union (ITU).
The key advantage of TLS is that it prevents anybody who is perhaps listening in on the info change from with the ability to learn the info within the clear. All attributable to it being encrypted.
Most often, fashionable Apple units and most software program working on Apple units mechanically know find out how to use TLS, so that you should not want to fret about it. So long as you employ an “https” connection when looking the online, TLS is computerized.
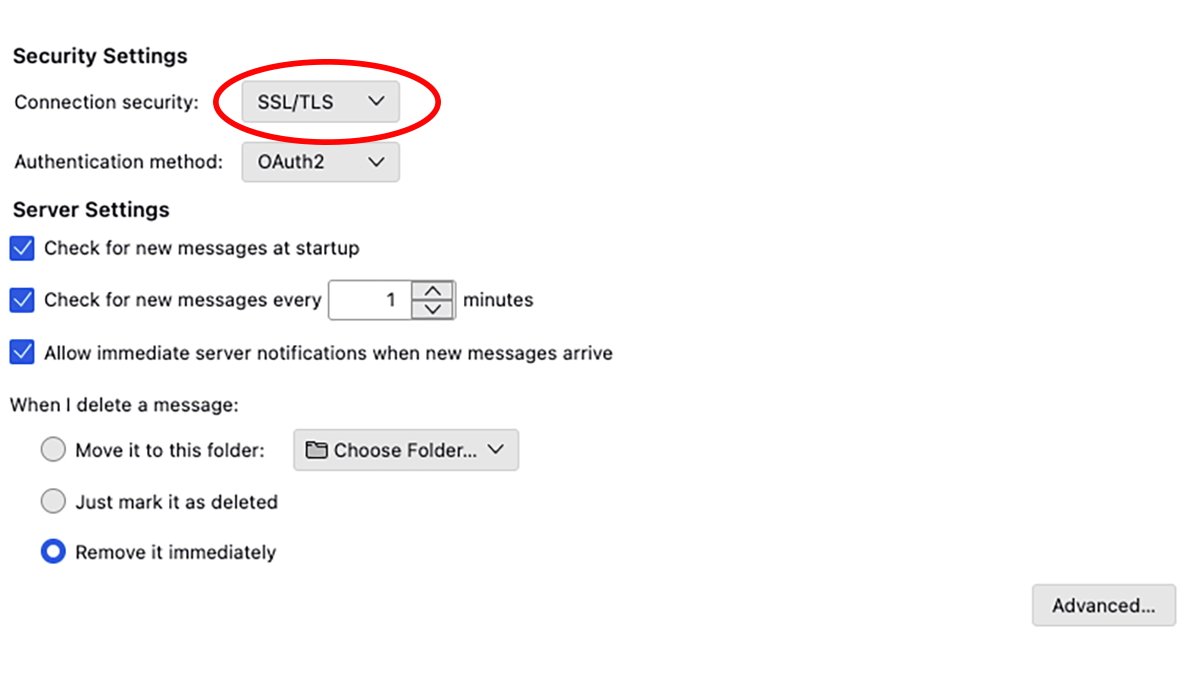
Some e mail consumer apps reminiscent of Mozilla Thunderbird help you specify TLS/SSL because the communication safety customary:
WPA/WPA2/WPA3 Enterprise and 802.1X
When WiFi networking first appeared on the finish of the final century, a brand new safety customary, WEP (Wired Equivalency Privateness) was developed to permit wi-fi networks to hook up with different units securely.
WEP had severe safety flaws, and in response, Wi-Fi Protected Entry (WPA) was produced. This protocol has undergone three revisions because the early 2000s, with the present model being WPA3.
Most fashionable WiFi units, together with Apple’s units, present WEP3 for connections.
Each Apple’s WiFi and Ethernet units additionally present for connections that use one other safety protocol referred to as 802.1X. This protocol is a part of the 802 community customary as outlined by IEEE, which covers each WiFi and Ethernet wired networks.
802.1X prevents a kind of community assault often called {Hardware} Addition, the place a malicious machine is used to connect to a community and carry out hacking actions. For instance, a small pc like a Raspberry Pi plugged right into a spare community port.
By way of using an authentication server, 802.1X can normally thwart such assaults by authenticating the person by way of WiFi, LAN, or WAN.
In in the present day’s world of units all over the place, {Hardware} Addition assaults are far more frequent than they was.
WPA is now not supported by modem variations of Apple’s working techniques, so typically, you will need to use WPA2, WPA3, or some variant thereof.
Login Window Mode (LWM) is a method to hook up with a safe community from the Mac’s login window if the community helps Listing Companies.
To be able to use LWM, you want a connection to an Lively Listing or Open Listing server. Additionally, you will want an put in Mac community configuration profile which allows LWM for the community you are making an attempt to hook up with.
As soon as configured, on the Mac Login Window, choose Different from the record of customers, then enter your Listing Companies person identify and password. From the popup menu, choose the community interface you need to join on (WiFi or Ethernet).
Lively Listing and Open Listing are applied sciences that enable person data and credentials to be saved on a central server for authentication. We’ll cowl Open Listing in an article within the close to future.
Most often, Apple has made community safety seamless so that you normally will not want to fret about it. The above applied sciences are principally all a part of internet or web requirements, and in most software program their use is computerized.