Samsung has revealed the way it makes Galaxy telephones and tablets safer. It’s by one thing known as Challenge Infinity, a mechanism that’s designed to seek out safety loopholes throughout the {hardware} and the software program and fixing them as quickly as potential.
Samsung’s Challenge Infinity makes Galaxy gadgets safe by coping with threats
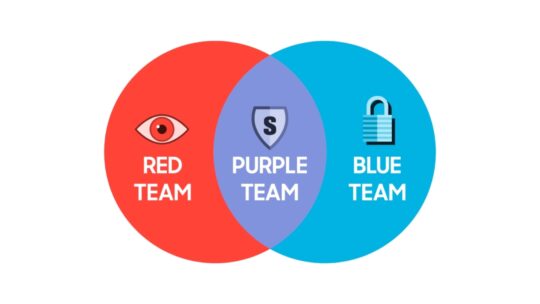
The Cyber Risk Intelligence (CTI) crew inside Samsung’s Challenge Infinity, together with Crimson (RED), Blue (BLUE), and Purple (PURPLE) groups, determine real-world situations to make Galaxy telephones and tablets safer.
RED and BLUE groups carry out proactive assault and protection capabilities to seek out safety loopholes in gadgets. The PURPLE crew does each assault and protection for sure important areas. These groups are unfold the world over, together with Brazil, Poland, Ukraine, and Vietnam.
The CTI crew is instantly concerned with safety updates that Samsung Galaxy gadgets get each month. Apparently, it explores Deep Net and Darkish Net areas, that are bustling markets for safety exploits, illicit hacking instruments, malware, ransomware, and spy ware. That is additionally the place you’ll find confidential data associated to companies and prospects.
As soon as a risk is found, the safety groups at Samsung work with builders and operators to lock every little thing down and repair the difficulty. Samsung additionally works with exterior members and companies to determine threats and safety loopholes. It’s providing a most reward (by way of Samsung Cellular Safety Rewards Program) quantity of $1 million to moral hackers or builders who can determine a number of vulnerabilities and assaults.
Justin Choi, VP and Head of the Safety Workforce at Samsung MX (Cellular eXperience), mentioned, “We intently monitor boards and marketplaces for mentions of zero-day or N-day exploits focusing on Galaxy gadgets, in addition to any leaked intelligence that would doubtlessly function an entry level for system infiltration.“